Pwnd By Polyfills
June 30, 2024A supply-chain attack by the new owners of the polyfill.io domain and project injected malware into over 100,000 websites recently.
The new owner of the project is Chinese and the original creator of the project posted the following on X/Twitter:
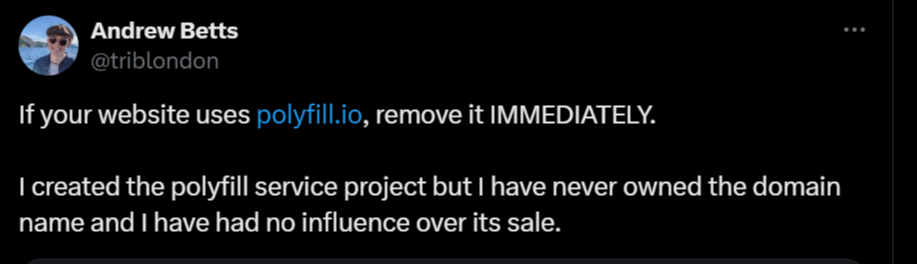
Polyfills for those that don’t know are ways of adding features to older browsers that are natively supported on newer versions. This particular attack targeted mobile devices as the way the CDN for polyfill.io worked was by looking at HTTP headers as the script was requested to decide what was loaded into the browser.
This demonstrates the level of trust placed in CDNs and third-party services simply by including a <script> tag in your site HTML. Serious consideration should be given to trusting potentially unknown actors just for the convenience of outsourcing the hosting of a resource you may not even need, as there is very little (if any) need for polyfills these days for example.
Using domains that are misspellings of (?) legitimate services (e.g. https://www.googie-anaiytics.com/ga.js) was part of the trick.
This has been reported on by SanSec and others. SanSec ended up getting DDOS’ed for their trouble.
Some other domains that also served malware apparently by the same actor are:
bootcdn.netbootcss.comstaticfile.netstaticfile.orgunionadjs.comxhsbpza.comunion.macoms.lanewcrbpc.com
It would be a good idea to check any and all projects for uses of cdn.polyfill.io and any of the above domains and remove them. For now NameCheap have suspended the domain and Cloudflare are doing real-time URL rewrites to their own version, which sounds like a good thing but demonstrates that should your domain end up on some kind of “naughty list” all it takes is two services to make a few changes and your site could either vanish or be seamlessly replaced with something else.
EOL